Our consulting services on the topic of Cyber Response Planning (CRP)
Cyber Response Planning (CRP)
Back in 2012, Robert Mueller (Director of the FBI) said: "There are only two types of companies. Those that have already been hacked and those that will be." In 2015, Jahn Chambers, then CEO of Cisco Systems, followed up and said: "There are only two types of companies. Those that have already been hacked and those that don't know they've been hacked."These statements are still as relevant as when they were made. According to the findings of recent surveys, only around 30 per cent of all companies have taken appropriate precautionary measures with regard to the detection, defence and management of cyber attacks. It takes around 200 days (according to the IBM Data Security Report 2022, an average of 277 days - around nine months) for IT security incidents to be detected.
 Cyberattacks have been steadily increasing for years and cause very high financial and reputational damage to affected companies. In Germany alone, the annual amount of damage rose from "still" 103 billion euros in 2019 to over 200 billion euros in 2022.
Cyberattacks have been steadily increasing for years and cause very high financial and reputational damage to affected companies. In Germany alone, the annual amount of damage rose from "still" 103 billion euros in 2019 to over 200 billion euros in 2022.
According to a recent study by IBM from 2022, a successful ransomware attack costs affected companies an average of 4.54 million US dollars. The ransom itself is not yet included in this sum.
Between 2021 and 2022, the amount of ransomware increased by around 13 per cent. That is more than in the previous five years combined. Nine out of ten companies (88 per cent) were affected by attacks in 2020/2021. In 2018/2019, three quarters (75 per cent) were victims. These are the findings of a representative study by the digital association Bitkom, for which more than 1,000 companies across all sectors were surveyed.
-
Malware (viruses, worms, etc. - sometimes polymorphic)
-
phishing
-
Distributed denial of service (DDoS)
-
SQL injection
-
Cross-site scripting (XSS)
In 2022, the industrial insurer Allianz Global Corporate & Specialty identified cyber incidents as the greatest business risk, well ahead of natural disasters or the outbreak of another pandemic.
Geopolitical crises such as the war in Ukraine and the trade war between the USA and China also play their part. Politically motivated cyberattacks are often carried out by state actors who may have considerably greater resources, both financial and technical. This enables the use of sophisticated attack methods, including APTs and zero-day exploits (previously unknown vulnerabilities) as well as advanced malware.
In the darknet/deep web, the underground economy has emerged in recent years, offering cybercrime-as-a-service. It has never been easier to get the "tools" for a cyberattack. The annual turnover of cybercrime-as-a-service is currently estimated at around 3 billion US dollars.
As a result of this ongoing massive threat situation, various updates/changes to legal and regulatory requirements have been or are being implemented. These are forcing more and more companies to consider the structured management of a cyber attack and to implement appropriate management systems.
The following should be emphasised here:
-
"Directive on measures for a high common level of cybersecurity across the Union" (NIS2 Directive)
-
Act on the implementation of EU NIS2 and strengthening cybersecurity (NIS2UmsuCG) - currently in draft form
-
IT Security Act 2.0
-
Digital Operational Resilience Act (DORA)
Our CRP consulting services
We work with you to develop customised solutions tailored to your requirements in this complex (IT) environment. We support you in setting up cyber response planning and cyber incident response management (CIRM). With our many years of experience, we support you in the introduction, further development or evaluation of your existing CRP or CIRM. Of course, we also consider the corresponding interfaces to other management disciplines such as business continuity management (BCM), IT service continuity management (ITSCM) and crisis management (CM).Our CRP coaching
When implementing projects, our IT experts always focus on building up in-house expertise. Our aim is for you to learn the necessary knowledge about the management process from us during the implementation of the project and to be able to put what you have learnt directly into practice afterwards. New processes are not always met with an undivided positive response. In our many years of experience, the best way to overcome internal scepticism is to create the necessary awareness among employees. In line with the quote from Antoine de Saint-Exupéry "If you want to build a ship, don't drum up men to procure wood, assign tasks and organise the work, but teach them to yearn for the vast, endless sea" - feel free to contact us if you need support in preparing and implementing awareness measures.What are the three most important arguments in favour of CRP?
Cyber Response Planning creates organisational and personnel structures for a fast and effective response to cyber attacks. This includes identifying the incident, containing the threat, restoring affected systems and minimising the impact on business operations.-
Rapid containment and minimising the impact can be critical to the survival of the business
-
Fulfilment of the requirements for "cyber insurance"
-
Compliance with legal and/or regulatory requirements
Why is CRP so important?
CRP is so important because it can make the difference between an effective response to a cyber attack and serious consequences for an organisation. It enables rapid detection of attacks and appropriate countermeasures to limit the damage.Companies that plan to take precautions often focus purely on the response to a cyberattack. This is problematic, as this is only one part of a comprehensive cybersecurity approach and lacks, for example, prevention and detection.
Cyber response planning therefore focuses not only on the response after an incident, but also on the prevention of attacks and the early detection of threats. Without a proactive strategy that integrates prevention, monitoring, detection and response, organisations are more vulnerable to attacks.
What exactly is CRP?
Cyber Response Planning (CRP) is the proactive and systematic planning and preparation of measures to respond effectively to cyber attacks. It is designed to anticipate security incidents and develop preparatory measures to prevent the occurrence of (IT) security incidents or at least minimise their impact.CRP is the basis for effective cyber incident response management. CRP therefore describes the "Preparation" phase in cyber incident response management. CRP is used to set up, test and improve CIRM. CRP also creates the ability to continuously monitor for attacks. This includes, among other things
-
Establishing an organisational structure for preparation and response
-
Ongoing identification and assessment of threats and cyber risks
-
Creating and updating detailed plans to be prepared for different types of cyber attacks
-
Use of security technologies and tools to detect and respond to incidents
-
Planning and conducting regular tests and simulation exercises
-
Regular training and awareness measures
And what are the aims of CRP?
CRP cannot completely prevent cyber attacks. There is no such thing as 100 per cent security, and it has to be honestly said that damage can occur. But it makes a significant difference whether there is a planned and tested response to cyber attacks or not. In principle, CRP pursues several key objectives. These include, among others-
Strengthening the company's resilience to cyber attacks
-
Minimising damage and reducing data loss, financial losses and disruption to operations
-
Ensuring business continuity and the survival of the company
-
Compliance with legal and regulatory requirements
-
Protecting reputation and customer trust
What advantages does a company with an established CRP have?
An established CRP offers companies a whole range of benefits. These include, among others-
Fast and effective response to cyber attacks
-
Minimising the impact and damage to the company
-
Security-conscious employees
-
Reduced costs by preventing cyber attacks
-
Greater resilience to cyber attacks
-
Compliance in the event of requirements from regulators and contractual partners
What does a CRP implementation look like?
Our qualified experts support the implementation or further development of your CRP using our process model, which combines all the requirements from the following standards and guidelines.-
National Institute of Standards and Technology, Special Publication 800-61, Revision 2, Computer Security Incident Handling Guide (NIST 800-61)
-
NIST Cybersecurity Framework
-
SANS Institute Guidelines
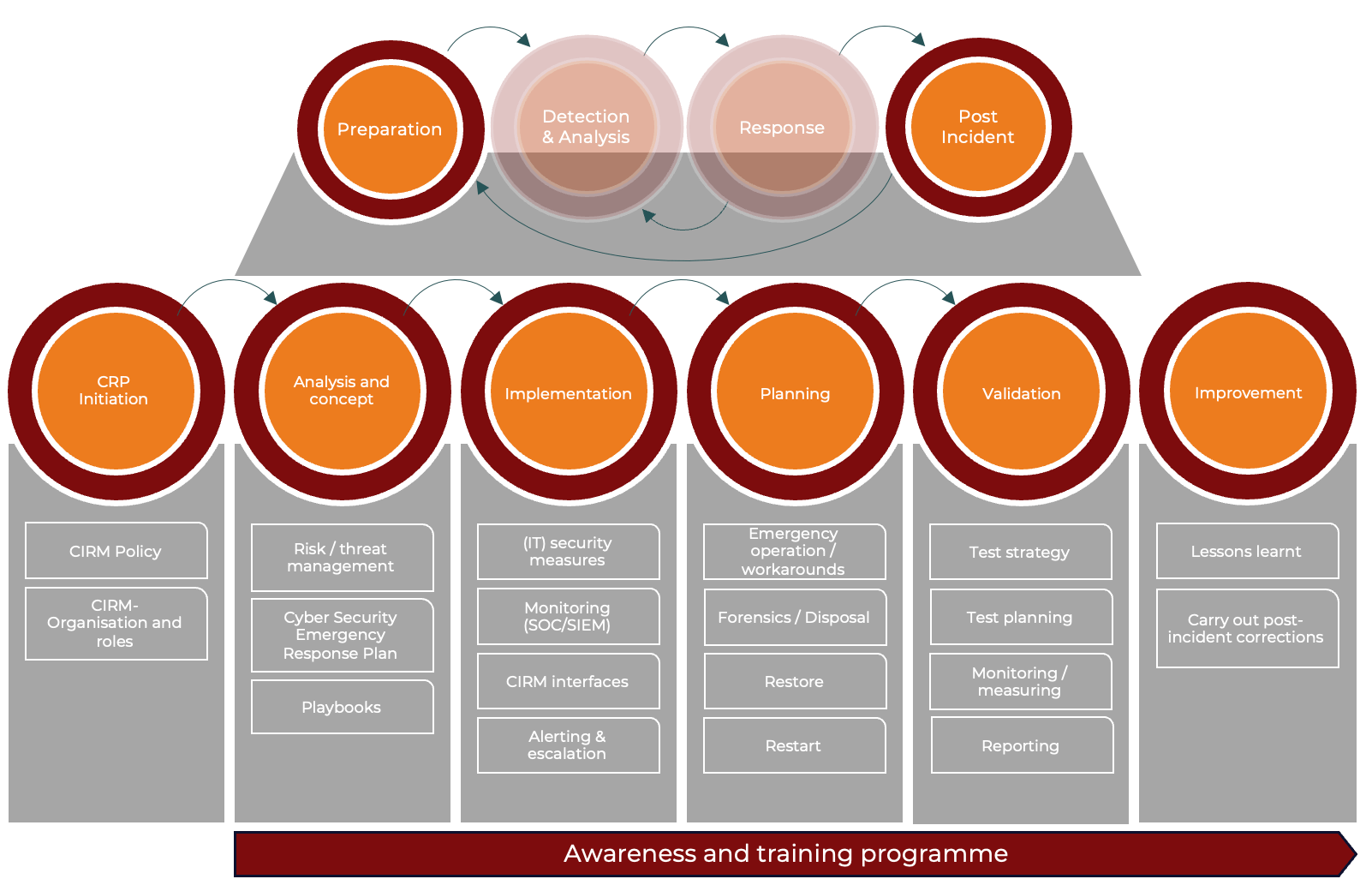
CRP initiation
Initiation is the basis for successful CRP implementation. The management commissions the implementation of the CRP in the company in the form of a CRP policy. The organisational structure and process steps are documented in the CRP policy. Furthermore, measures for maintaining the CRP process, its monitoring and its continuous improvement are defined.Analysis and concept
In the analysis phase, all current threats and attack scenarios are identified and analysed. The likelihood of a risk materialising and the impact it would have if it did occur are assessed. The playbooks are adapted according to the threats identified.Implementation
The implementation phase in the CRP is the step in which the planned (IT) security measures are operationalised. This includes all measures for protection, prevention, detection and alerting/escalation, such as the Security Operation Centre (SOC), SIEM and technical monitoring. This phase is crucial, as it is here that the theoretical and strategic considerations and results of the previous phases are transformed into concrete measures and changes within the organisation.Planning
During the planning phase, a detailed and documented plan is drawn up for a possible emergency operation, the procedure for cleaning up the systems, restoring data and restarting the IT infrastructures, IT systems and applications.Validation
The validation phase of the CRP checks whether the implemented monitoring and (IT) security measures are effective, efficient and appropriate. This phase includes regular tests and audits. This phase is crucial for the continuous improvement of the security level and ensures that the organisation can respond to new challenges and changing threats. Regular validation and adjustment of security strategies are essential to maintain a high level of cyber security.Improvement
The Improvement phase is aimed at continuously improving the organisation's cyber response planning process and cyber incident response management. Continuous improvement (CIP or PDCA cycle) is the core principle of all modern management systems. The results from the validation phase of the CRP and the post-incident phase from the management of incidents that have occurred flow into this phase. All information is used to identify potential for improvement. Continuous improvements increase the overall effectiveness of the CRP and CIRM.Awareness and training programme
The implementation of regular awareness and training measures are crucial components in the context of cyber response planning. Over 80 per cent of successful cyber attacks can be traced back to human error. Training and awareness-raising measures enable employees to recognise potential cyber threats and respond to them correctly. CRP training prepares employees to respond quickly and effectively to incidents, which helps to minimise damage.A company that invests in training its employees demonstrates its commitment to cyber security, which strengthens the trust of customers and partners.