Advice on information security
Information Security Management
The protection of sensitive company data is becoming increasingly important as digitalisation continues and customers and partners become more and more integrated into company processes. This makes the protection of this sensitive information all the more important. Information is a company asset, no matter what form it takes. Information is created when data is analysed and processed to give it a structure that can be understood and interpreted by people. Information is therefore processed data that has context, relevance and purpose.
Information is a company asset, no matter what form it takes. Information is created when data is analysed and processed to give it a structure that can be understood and interpreted by people. Information is therefore processed data that has context, relevance and purpose.
In the context of information security, it is primarily about protecting information, i.e. processed data that is important to your organisation in some way. However, the underlying data also plays an important role. If data is not secured at an early stage of its lifecycle, the resulting information can be jeopardised.
However, classic information security risks include not only deliberate actions, but also elementary threats such as fire, water, storms, earthquakes and failed software updates. In other words, anything that can jeopardise the so-called protection goals such as availability, integrity and confidentiality. The main focus of this approach is to reduce risks to information and, in particular, to ensure the integrity, availability and confidentiality of data and information at all times.
The complexity of information security should be easy for you to use at all times. That is why we help you as a partner to ensure the greatest possible benefit without neglecting the protective effect or conformity to standards. We are at your side at all times as a coach and sparring partner.
Our ISM consulting services
We work with you to develop customised solutions tailored to your requirements in this complex (IT) environment. We support you in setting up an ISM system or further developing an existing system. With our many years of experience, we support you in the introduction, further development and/or evaluation of your existing information security management system (ISMS). It goes without saying that we also consider the corresponding interfaces to other management disciplines such as Business Continuity Management (BCM), IT Service Continuity Management (ITSCM), Cyber Incident Response Management (CIRM) and Crisis Management (KM).If certification is imminent, we are happy to help you as an independent consultancy to determine your readiness for certification and, if necessary, to find suitable solutions. Our experts and auditors have their finger on the pulse and follow the current trends and requirements in ISM for you in accordance with the current standards (ISO 27001 and BSI IT-Grundschutz). Our experts also provide support in reviewing the requirements for operators of critical infrastructures in connection with the obligation to provide evidence in accordance with Section 8a (3) BSIG and secure grid operation in accordance with Section 11 (1a) EnWG.
Our ISM coaching
When implementing projects, our IT experts always focus on building up in-house expertise. Our aim is for you to learn the necessary knowledge about the management process from us during the implementation of the project and to be able to put what you have learnt directly into practice afterwards. New processes are not always met with an undivided positive response. In our many years of experience, the best way to overcome internal scepticism is to create the necessary awareness among employees. In line with the quote from Antoine de Saint-Exupéry "If you want to build a ship, don't drum up men to procure wood, assign tasks and organise the work, but teach them to yearn for the vast, endless sea" - feel free to contact us if you need support in preparing and implementing awareness measures.What are the three most important arguments in favour of ISM?
ISM as a management process creates organisational and personnel structures to prevent (IT) security incidents. Overall, ISM is not just a question of IT security, but a strategic necessity that affects all business operations. An established information security management system sends an important message to the market. It creates trust among customers, suppliers and other service providers with regard to-
the protection of sensitive data and confidential information such as personal data, financial information and intellectual property
-
compliance with legal and regulatory requirements
-
the completion of projects and services within the planned or promised timeframe
Why is ISM so important?
Information is one of the most important intangible assets of an organisation. Therefore, information must be adequately protected by combining systems, processes and internal controls to ensure the integrity and confidentiality of data and operating procedures in an organisation. Purely technical protection using firewall systems, for example, is no longer sufficient and must be accompanied by organisational measures. From targeted social engineering attacks to advanced malware techniques and elementary hazards such as earthquakes or floods - the threats are many and varied. The issue of corporate data security must be considered strategically. Setting up an ISMS often presents companies with major challenges, as they lack the expertise within their own ranks. However, without an established ISMS, there are incalculable risks for your company's assets and production processes.What exactly is ISM?
Information security is a management system that provides processes for the protection of information, regardless of its type and origin. This includes, among other things, the establishment of an appropriate security organisation, the creation of a security concept, the definition of generic security objectives and the identification, assessment and mitigation of information risks. In practice, the aim is to prevent or at least reduce the likelihood of unauthorised/inappropriate access to data or the unlawful use, disclosure, interruption, deletion, falsification, modification, review, recording or devaluation of information. This also includes measures aimed at minimising the negative impact of such incidents.Information security is the protection of information with the aim of ensuring the continuity of business operations and minimising business risks.
What are ISM's goals?
The main focus of information security is on compliance with the defined security objectives for company data. The best-known security objectives are compliance with confidentiality, integrity, availability (continuity) and authenticity of information. However, classic information security risks include not only deliberate actions, but also elementary threats such as fire, water, storms, earthquakes and failed software updates.What advantages does a company with an established ISM have?
Information security incidents often cause extremely high financial and/or reputational damage to a company. The financial damage can very quickly run into the millions. There are plenty of examples and they can be found in the relevant media. The probability of a security incident occurring can be massively reduced by an established ISMS. But even if you are affected by a security incident, the impact is far less than if your company is caught unprepared. The proactive orientation of an ISMS enables you to recognise potential vulnerabilities at an early stage and take appropriate countermeasures. Through continuous monitoring and regular audits, you can also ensure that your security measures adapt to constantly changing threats.Companies with an established ISM have:
-
competitive advantages, as a well-established ISMS cannot be a differentiating feature in the market
-
a high level of security to protect their sensitive and confidential information from theft, loss and manipulation
-
security-conscious employees
-
reduced costs through the prevention of (IT) security incidents
-
greater resilience to unexpected (IT) security incidents
-
compliance in the event of requirements from regulators and contractual partners
What does an ISM implementation look like?
Our qualified experts provide support with the implementation or further development of your ISMS using our process model, which combines all the requirements of ISO 27001 and the modular principle of BSI IT baseline protection.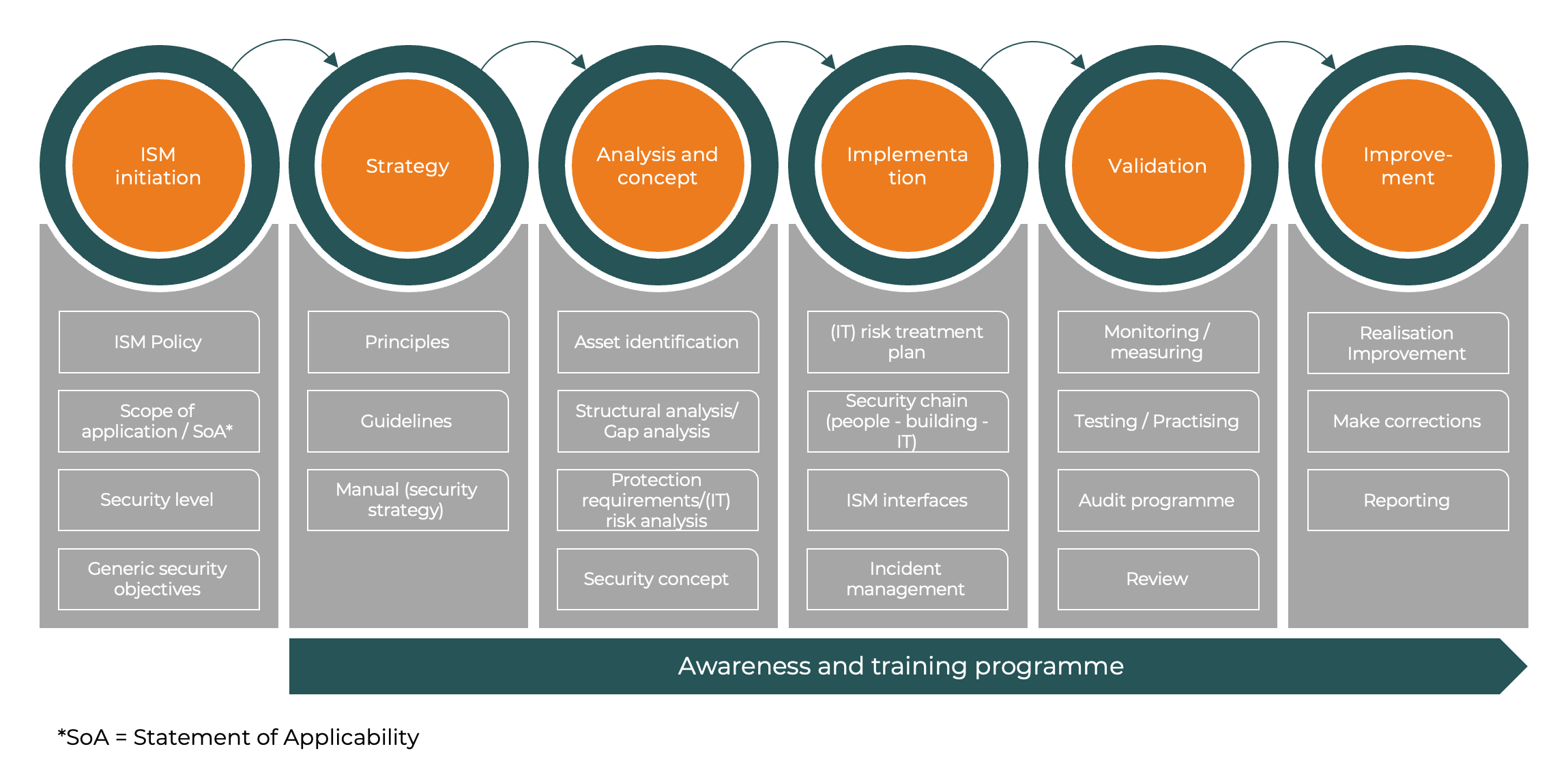
ISM initiation
Initiation is the basis for successful ISM implementation. Management commissions the implementation of ISM in the company in the form of an ISM policy. The ISM policy defines the organisational structure, the security objectives to be considered, the security level to be achieved and documents the required process steps. It also defines measures for maintaining the ISM process, its monitoring and its continuous improvement.ISM strategy
In the strategy phase, the process organisation is defined and the routine tasks and activities are documented. The applicable principles and standard operating procedures (SOPs) are also developed.Analysis and concept
In the analysis phase, all key components and resources of the organisation are identified and the respective criticality is determined with regard to the defined security objectives (e.g. confidentiality, integrity and availability) in order to determine the level of protection required. Potential threats and vulnerabilities are identified and analysed as part of the risk analysis. It assesses how likely it is that a risk will materialise and what impact it would have if it did occur.Implementation
The implementation phase in ISM is the step in which the planned security strategies, policies and controls are put into practice. This phase is crucial because it is here that the theoretical and strategic considerations and results of the previous phases (such as ISM strategy and analysis and concept) are transformed into concrete measures and changes within the organisation.Validation
In the validation phase of the ISM, it is checked whether the implemented security measures are effective, efficient and appropriate to meet the organisation's security objectives. This phase includes regular tests and audits. This phase is crucial for the continuous improvement of the security level and ensures that the organisation can react to new challenges and changing threats. Regular validation and adjustment of security strategies are essential to maintain a high level of information security.Improvement
The improvement phase is aimed at continuously improving the organisation's information security. Continuous improvement (CIP or PDCA cycle) is the core principle of all modern management systems. The results from the validation phase flow into this phase and are used to identify potential for improvement. Continuous improvements increase the overall effectiveness of the ISMS.Awareness and training programme
The implementation of regular awareness and training programmes are crucial components in the context of information security. An effective awareness and training programme helps to minimise risks as employees are better able to identify security risks and act appropriately. This is crucial as human factors are often the weakest links in the safety chain.In the long term, these measures help to create a culture of safety within the organisation in which safety is seen as a shared responsibility.